From the Analog to the Digital Age
The Digital Basis of Computers: Electrical Signals as Discontinuous Bursts
What does “digital” means?
- Digital describes any system based on discontinuous data or events; in the case of computers, it refers to communications signals or information represented in a two-state (binary) way using electronic or electromagnetic signals. Each 0 and 1 signal represents a bit. Describes any system based on discontinuous data or events. Computers are digital machines because at their most basic level they can distinguish between just two values, 0 and 1, or off and on. There is no simple way to represent all the values in between, such as 0.25. All data that a computer processes must be encoded digitally, as a series of zeroes and ones. http://www.webopedia.com/TERM/D/digital.html

The Analog Basis of Life: Electrical Signals as Continuous Waves
What does “analog” means?
- Analog continuously varying in strength and/or quality–fluctuating, evolving, or continually changing. Describes a device or system that represents changing values as continuously variable physical quantities. A typical analog device is a clock in which the hands move continuously around the face. http://www.webopedia.com/TERM/A/analog.html

Purpose of the Dial-Up Modem: Converting Digital Signals to Analog Signals & Back
How does a telephone modem change analog to digital signals and the reverse?
- Modem is short for “modulate/demodulate”; a sending modem modulates digital signals for transmission over phone lines. A receiving modem demodulates the analog signals back into digital signals. A modem is a device or program that enables a computer to transmit data over, for example, telephone or cable lines. Computer information is stored digitally, whereas information transmitted over telephone lines is transmitted in the form of analog waves. A modem converts between these two forms. http://www.webopedia.com/TERM/M/modem.html

Converting Reality to Digital Form
How is sampling used to express analog reality in digital form?
- The digital uses a device (called an analog-to-digital converter) to record representatives selections, or samples, of the sounds and convert the analog waves into a stream of numbers that the computer then uses to express the sounds.
- The most important is that all kinds of multimedia can now be changed into digital form and transmitted as data to all kinds of devices
Network
What are the benefit of networks, and what are their types, components, and variations?
- Network or communications network, is a system of interconnected computers, telephones, or other communications devices that can communicate with one another and share applications and data. A network is a series of points or nodes interconnected by communication paths. http://searchnetworking.techtarget.com/definition/network

The Benefits of Networks
What are five ways I might benefit from networks?
- SHARING OF PERIPHERAL DEVICES
- SHARING OF PROGRAMS & DATA
- BETTER COMMUNICATIONS
- SECURITY OF INFORMATION
- ACCESS TO DATABASES
Types of Networks: WANs, MANs, LANs, HANs, PANs, & others
How do the sizes of networks differ?
- WIDE AREA NETWORK
- WAN is a communications network that covers a wide geographic area, such as a country or the world. The computers are farther apart and are connected by telephone lines or radio waves. http://www.webopedia.com/TERM/N/network.html

- WAN is a communications network that covers a wide geographic area, such as a country or the world. The computers are farther apart and are connected by telephone lines or radio waves. http://www.webopedia.com/TERM/N/network.html
- METROPOLITAN AREA NETWORK
- MAN is a communications network covering a city or a suburb. A data network designed for a town or city. http://www.webopedia.com/TERM/N/network.html

- MAN is a communications network covering a city or a suburb. A data network designed for a town or city. http://www.webopedia.com/TERM/N/network.html
- LOCAL AREA NETWORK
- LAN or local net, connects computers and devices in a limited geographic area, such as one office, one building, or a group of buildings close together. The computers are geographically close together (that is, in the same building). http://www.webopedia.com/TERM/N/network.html

- LAN or local net, connects computers and devices in a limited geographic area, such as one office, one building, or a group of buildings close together. The computers are geographically close together (that is, in the same building). http://www.webopedia.com/TERM/N/network.html
- HOME AREA NETWORK
- HAN uses wired, cable, or wireless connections to link a household’s digital devices. A network contained within a user’s home that connects a person’s digital devices. http://www.webopedia.com/TERM/N/network.html

- HAN uses wired, cable, or wireless connections to link a household’s digital devices. A network contained within a user’s home that connects a person’s digital devices. http://www.webopedia.com/TERM/N/network.html
- PERSONAL AREA NETWORK
- PAN uses short-range wireless technology to connect an individual’s personal electronics. a computer network used for data transmission among devices such as computers, telephones and personal digital assistants. en.wikipedia.org/wiki/Personal_area_network

- PAN uses short-range wireless technology to connect an individual’s personal electronics. a computer network used for data transmission among devices such as computers, telephones and personal digital assistants. en.wikipedia.org/wiki/Personal_area_network
- HOME AUTOMATION NETWORK
- Relies on very inexpensive, very short-range, low-power wireless technology in the under-200-Kbps range to link switches and sensors around the house. a type of local area network that develops from the need to facilitate communication and interoperability among digital devices present inside or within the close vicinity of a home. Devices capable of participating in this network–smart devices such as network printers and handheld mobile computers–often gain enhanced emergent capabilities through their ability to interact. These additional capabilities can then be used to increase the quality of life inside the home in a variety of ways, such as automation of repetitious tasks, increased personal productivity, enhanced home security, and easier access to entertainment. http://en.wikipedia.org/wiki/Home_network

- Relies on very inexpensive, very short-range, low-power wireless technology in the under-200-Kbps range to link switches and sensors around the house. a type of local area network that develops from the need to facilitate communication and interoperability among digital devices present inside or within the close vicinity of a home. Devices capable of participating in this network–smart devices such as network printers and handheld mobile computers–often gain enhanced emergent capabilities through their ability to interact. These additional capabilities can then be used to increase the quality of life inside the home in a variety of ways, such as automation of repetitious tasks, increased personal productivity, enhanced home security, and easier access to entertainment. http://en.wikipedia.org/wiki/Home_network
How Networks Are Structured: Client/Server & Peer to Peer
What’s the difference between client/server and peer to peer networks?
- CLIENT/SERVER NETWORKS
- Consists of clients, which are microcomputers that request data, and servers, which are computers used to supply data. A computer network in which one centralized, powerful computer (called the server) is a hub to which manyless powerful personal computers or workstations (called clients) are connected. The clients run programs and access data that are stored on the server. http://www.thefreedictionary.com/client%2Fserver+network

- File server – is a computer that acts like a disk drive, storing the programs and data files shared by users on a LAN. A computer attached to a network that has the primary purpose of providing a location for shared disk access, i.e. shared storage of computer files (such as documents, sound files, photographs, movies, images, databases, etc.) that can be accessed by the workstations that are attached to the same computer network. http://en.wikipedia.org/wiki/File_server

- Database Server – is a computer in a LAN that stores data but doesn’t store programs. A database server is a computer program that provides database services to other computer programs or computers, as defined by the client–server model. The term may also refer to a computer dedicated to running such a program. en.wikipedia.org/wiki/Database_server

- Print Server – controls one or more printers and stores the print-image output from all the microcomputers on the system. A print server, or printer server, is a device that connects printers to client computers over a network. It accepts print jobs from the computers and sends the jobs to the appropriate printers, queuing the jobs locally to accommodate the fact that work may arrive more quickly than the printer can actually handle it. en.wikipedia.org/wiki/Print_server

- File server – is a computer that acts like a disk drive, storing the programs and data files shared by users on a LAN. A computer attached to a network that has the primary purpose of providing a location for shared disk access, i.e. shared storage of computer files (such as documents, sound files, photographs, movies, images, databases, etc.) that can be accessed by the workstations that are attached to the same computer network. http://en.wikipedia.org/wiki/File_server
- Consists of clients, which are microcomputers that request data, and servers, which are computers used to supply data. A computer network in which one centralized, powerful computer (called the server) is a hub to which manyless powerful personal computers or workstations (called clients) are connected. The clients run programs and access data that are stored on the server. http://www.thefreedictionary.com/client%2Fserver+network
- PEER-TO-PEER NETWORKS
- Peer-to-peer (P2P) network – all microcomputers on the network communicate directly with one another without relying on a server. Peer-to-peer (P2P) computing or networking is a distributed application architecture that partitions tasks or work loads between peers. http://en.wikipedia.org/wiki/Peer-to-peer

- Peer-to-peer (P2P) network – all microcomputers on the network communicate directly with one another without relying on a server. Peer-to-peer (P2P) computing or networking is a distributed application architecture that partitions tasks or work loads between peers. http://en.wikipedia.org/wiki/Peer-to-peer
Intranets, Extranets, & VPNs
What are the difference among intranets, extranets, and VPNs?
- INTRANETS: FOR INTERNAL USE ONLY
- Intranet is an organization’s internal private network that uses the infrastructure and standards of the internet and the web. A computer network that uses Internet Protocol technology to share information, operational systems, or computing services within an organization. This term is used in contrast to extranet, a network between organizations, and instead refers to a network within an organization. Sometimes, the term refers only to the organization’s internal website, but may be a more extensive part of the organization’s information technology infrastructure, and may be composed of multiple local area networks. The objective is to organize each individual’s desktop with minimal cost, time and effort to be more productive, cost efficient, timely, and competitive. http://en.wikipedia.org/wiki/Intranet

- Intranet is an organization’s internal private network that uses the infrastructure and standards of the internet and the web. A computer network that uses Internet Protocol technology to share information, operational systems, or computing services within an organization. This term is used in contrast to extranet, a network between organizations, and instead refers to a network within an organization. Sometimes, the term refers only to the organization’s internal website, but may be a more extensive part of the organization’s information technology infrastructure, and may be composed of multiple local area networks. The objective is to organize each individual’s desktop with minimal cost, time and effort to be more productive, cost efficient, timely, and competitive. http://en.wikipedia.org/wiki/Intranet
- EXTRANETS: FOR CERTAIN OUTSIDERS
- Extranet are private intranets that connects not only internal personnel but also selected suppliers and other strategic parties. a computer network that allows controlled access from outside of an organization’s intranet. Extranets are used for specific use cases including business-to-business (B2B). In a business-to-business context, an extranet can be viewed as an extension of an organization’s intranet that is extended to users outside the organization, usually partners, vendors and suppliers, in isolation from all other Internet users. It is in context of that isolation that an extranet is different from an intranet or internet. In contrast, business-to-consumer (B2C) models involve known servers of one or more companies, communicating with previously unknown consumer users. An extranet is similar to a DMZ in that it provides access to needed services for channel partners, without granting access to an organization’s entire network. http://en.wikipedia.org/wiki/Extranet

- Extranet are private intranets that connects not only internal personnel but also selected suppliers and other strategic parties. a computer network that allows controlled access from outside of an organization’s intranet. Extranets are used for specific use cases including business-to-business (B2B). In a business-to-business context, an extranet can be viewed as an extension of an organization’s intranet that is extended to users outside the organization, usually partners, vendors and suppliers, in isolation from all other Internet users. It is in context of that isolation that an extranet is different from an intranet or internet. In contrast, business-to-consumer (B2C) models involve known servers of one or more companies, communicating with previously unknown consumer users. An extranet is similar to a DMZ in that it provides access to needed services for channel partners, without granting access to an organization’s entire network. http://en.wikipedia.org/wiki/Extranet
- VIRTUAL PRIVATE NETWORKS
- VPNs private networks that use a public network (usually the internet) to connect remote sites. VPN is a network that is constructed by using public wires — usually the Internet — to connect to a private network, such as a company’s internal network. There are a number of systems that enable you to create networks using the Internet as the medium for transporting data. These systems use encryption and other securitymechanisms to ensure that only authorized users can access the network and that the data cannot be intercepted. http://www.webopedia.com/TERM/V/VPN.html

- VPNs private networks that use a public network (usually the internet) to connect remote sites. VPN is a network that is constructed by using public wires — usually the Internet — to connect to a private network, such as a company’s internal network. There are a number of systems that enable you to create networks using the Internet as the medium for transporting data. These systems use encryption and other securitymechanisms to ensure that only authorized users can access the network and that the data cannot be intercepted. http://www.webopedia.com/TERM/V/VPN.html
Components of a Network
What are the various parts of a network?
- WIRED AND/OR WIRELESS CONNECTIONS
- HOSTS & NODES

- Host computer a mainframe or midsize central computer that controls the network. The main computer in a network: controls or performs certain functions for other computers. http://dictionary.reference.com/browse/host+computer
- Node is any device that is attached to a network−for example, a microcomputer, terminal, storage device, or printer. is either a connection point, a redistribution point or a communication endpoint (some terminal equipment). The definition of a node depends on the network and protocol layer referred to. http://en.wikipedia.org/wiki/Node_(networking)
- PACKETS
- Packets is a fixed-length block of data for transmission. A piece of a message transmitted over a packet-switching network. See under packet switching. One of the key features of a packet is that it contains the destination address in addition to the data. In IP networks, packets are often called datagrams. http://www.webopedia.com/TERM/P/packet.html

- Packets is a fixed-length block of data for transmission. A piece of a message transmitted over a packet-switching network. See under packet switching. One of the key features of a packet is that it contains the destination address in addition to the data. In IP networks, packets are often called datagrams. http://www.webopedia.com/TERM/P/packet.html
- PROTOCOLS
- Protocol or communications protocol, is a set of conventions governing the exchange of data between hardware and/or software components in a communications network. Is the special set of rules that end points in a telecommunication connection use when they communicate. http://searchnetworking.techtarget.com/definition/protocol
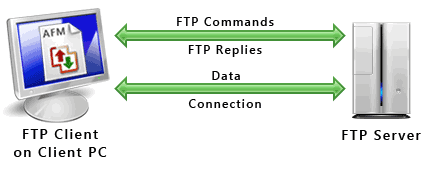
- Protocol or communications protocol, is a set of conventions governing the exchange of data between hardware and/or software components in a communications network. Is the special set of rules that end points in a telecommunication connection use when they communicate. http://searchnetworking.techtarget.com/definition/protocol
- NETWORKS LINKING DEVICES: HUB, SWITCHES, BRIDGES, GATEWAYS, ROUTERS, & BACKBONES
- Hubs is a common connections point for devices in a network−a place of convergence where data arrives from one or more directions and is forwarded out in one or more other directions. A common connection point for devices in a network. Hubs are commonly used to connect segments of a LAN. A hub contains multiple ports. When a packet arrives at one port, it is copied to the other ports so that all segments of the LAN can see all packets. http://www.webopedia.com/TERM/H/hub.html

- Switches is a devices that connects computers to a network. In networks, a device that filters and forwardspackets between LAN segments. Switches operate at the data link layer (layer 2) and sometimes the network layer (layer 3) of the OSI Reference Model and therefore support any packet protocol. LANs that use switches to join segments are called switched LANs or, in the case of Ethernet networks, switched Ethernet LANs. http://www.webopedia.com/TERM/S/switch.html

- Bridges is an interface used to connect the same types of networks. A device that connects two local-area networks (LANs), or two segments of the same LAN that use the same protocol, such as Ethernet or Token-Ring. http://www.webopedia.com/TERM/B/bridge.html

- Gateways is an interface permitting communication between dissimilar networks. A node on a network that serves as an entrance to another network. In enterprises, the gateway is the computer that routes the traffic from a workstation to the outside network that is serving the Web pages. In homes, the gateway is the ISPthat connects the user to the internet. http://www.webopedia.com/TERM/G/gateway.html

- Routers is a special computer that directs communicating messages when several networks are connected together. A router is a device that forwards data packets alongnetworks. A router is connected to at least two networks, commonly two LANs or WANs or a LAN and its ISP’s network. Routers are located at gateways, the places where two or more networks connect. http://www.webopedia.com/TERM/R/router.html

- Backbones consists of main highway−including gateways, routers, and other communications equipment−that connects all computer networks in an organization. Another term for bus, the main wire that connects nodes. The term is often used to describe the main network connections composing the Internet. http://www.webopedia.com/TERM/B/backbone.html

- Hubs is a common connections point for devices in a network−a place of convergence where data arrives from one or more directions and is forwarded out in one or more other directions. A common connection point for devices in a network. Hubs are commonly used to connect segments of a LAN. A hub contains multiple ports. When a packet arrives at one port, it is copied to the other ports so that all segments of the LAN can see all packets. http://www.webopedia.com/TERM/H/hub.html
- NETWORK INTERFACE CARDS
- NETWORKS OPERATING SYSTEM
Network Topologies: Bus, Ring, & Star
What are three popular configurations for networks?
– The logical layout, or shape, of a network is called a topology. In communication networks, a topology is a usually schematic description of the arrangement of a network, including its nodes and connecting lines. There are two ways of defining network geometry: the physical topology and the logical (or signal) topology. http://en.wikipedia.org/wiki/Topology
- BUS NETWORK
- All nodes are connected to a single wire or cable, the bus, which has two endpoints Each communications device on the network transmits electronic messages to other devices. A bus network is a network topology in which nodes are connected in a daisy chain by a linear sequence of buses. en.wikipedia.org/wiki/Bus_network
- RING NETWORK
- Is one in which all microcomputers and other communications devices are connected in a continuous loop. A ring network is a network topology in which each node connects to exactly two other nodes, forming a single continuous pathway for signals through each node – a ring. Data travel from node to node, with each node along the way handling every packet. en.wikipedia.org/wiki/Ring_network
- STAR NETWORK
- Is one in which all microcomputers and other communications devices are directly connected to a central server. Star networks are one of the most common computer network topologies. In its simplest form, a star network consists of one centralswitch, hub or computer, which act as a conduit to transmit messages. This consists of a central node, to which all other nodes are connected; this central node provides a common connection point for all nodes through a hub. en.wikipedia.org/wiki/Star_network
Two Ways to Prevent Messages from Colliding: Ethernet & Token Ring
How do the two methods of keeping messages from colliding work?
- ETHERNET
- Is a LAN technology that can be used with almost any kind of computer and that describes how data can be sent in packets in between computers an other networked devices usually in close proximity. a family of computer networking technologies for local area (LAN) and larger networks. http://en.wikipedia.org/wiki/Ethernet

- Is a LAN technology that can be used with almost any kind of computer and that describes how data can be sent in packets in between computers an other networked devices usually in close proximity. a family of computer networking technologies for local area (LAN) and larger networks. http://en.wikipedia.org/wiki/Ethernet
- TOKEN RING
- Is a LAN technology that transmits a special control message frame. A type of computer network in which all the computers are arranged (schematically) in a circle. A token, which is a special bit pattern, travels around the circle. To send a message, a computer catches the token, attaches a message to it, and then lets it continue to travel around the network. http://www.webopedia.com/TERM/T/token_ring_network.html

- Is a LAN technology that transmits a special control message frame. A type of computer network in which all the computers are arranged (schematically) in a circle. A token, which is a special bit pattern, travels around the circle. To send a message, a computer catches the token, attaches a message to it, and then lets it continue to travel around the network. http://www.webopedia.com/TERM/T/token_ring_network.html
Wired Communication Media
What are types of wired communications media?
- Communications media or communications channels, carry signals over a communications path, the route between two or more communications media devices. Communication media refers to the means of delivering and receiving data or information. In telecommunication, these means are transmission and storage tools or channels for data storage and transmission. http://www.techopedia.com/definition/14462/communication-media


Wired Communications Media: Wires & Cables
What is the difference between the three types of wired communications media?
- TWISTED-PAIR WIRE
- Consists of two strands of insulated copper wire, twisted around each other. This twisted-pair configuration (compared to the straight wire) somewhat reduces interference (called “crosstalk”) from electrical fields. Twisted pair cabling is a type of wiring in which two conductors of a single circuit are twisted together for the purposes of canceling out electromagnetic interference from external sources; for instance, electromagnetic radiation from unshielded twisted pair cables, and crosstalk between neighboring pairs. en.wikipedia.org/wiki/Twisted_pair

- Consists of two strands of insulated copper wire, twisted around each other. This twisted-pair configuration (compared to the straight wire) somewhat reduces interference (called “crosstalk”) from electrical fields. Twisted pair cabling is a type of wiring in which two conductors of a single circuit are twisted together for the purposes of canceling out electromagnetic interference from external sources; for instance, electromagnetic radiation from unshielded twisted pair cables, and crosstalk between neighboring pairs. en.wikipedia.org/wiki/Twisted_pair
- COAXIAL CABLE
- Commonly called “coax,” is a high-frequency transmission cable of insulated copper wire wrapped in a solid or braided metal shield and then in an external plastic cover. Coaxial cable is the kind of copper cable used by cable TV companies between the community antenna and user homes and businesses. searchdatacenter.techtarget.com/definition/coaxial-cable

- Commonly called “coax,” is a high-frequency transmission cable of insulated copper wire wrapped in a solid or braided metal shield and then in an external plastic cover. Coaxial cable is the kind of copper cable used by cable TV companies between the community antenna and user homes and businesses. searchdatacenter.techtarget.com/definition/coaxial-cable
- FIBER-OPTIC CABLE
- Consists of dozens or hundreds of thin strands of glass or plastic that transmit pulsating beams of light rather than electricity. A technology that uses glass (or plastic) threads (fibers) to transmit data. A fiber optic cable consists of a bundle of glass threads, each of which is capable of transmitting messages modulated onto light waves. http://www.webopedia.com/TERM/F/fiber_optics.html

- Consists of dozens or hundreds of thin strands of glass or plastic that transmit pulsating beams of light rather than electricity. A technology that uses glass (or plastic) threads (fibers) to transmit data. A fiber optic cable consists of a bundle of glass threads, each of which is capable of transmitting messages modulated onto light waves. http://www.webopedia.com/TERM/F/fiber_optics.html
Wired Communication Media for Homes: Ethernet, HomePNA, & HomePlug
What is the difference between the three types of wired communications media used for home networks?
- ETHERNET
- HOMEPNA: USING THE HOME’S EXISTING TELEPHONE WIRING
- Technology, a standard that allows a household to use a home’s existing telephone wiring for a home network. The HomePNA Alliance (formerly the Home Phoneline Networking Alliance, also known as HPNA) is an incorporated non-profit industry association of companies that develops and standardizes technology for home networking over the existing coaxial cables and telephone wiring within homes. en.wikipedia.org/wiki/HomePNA
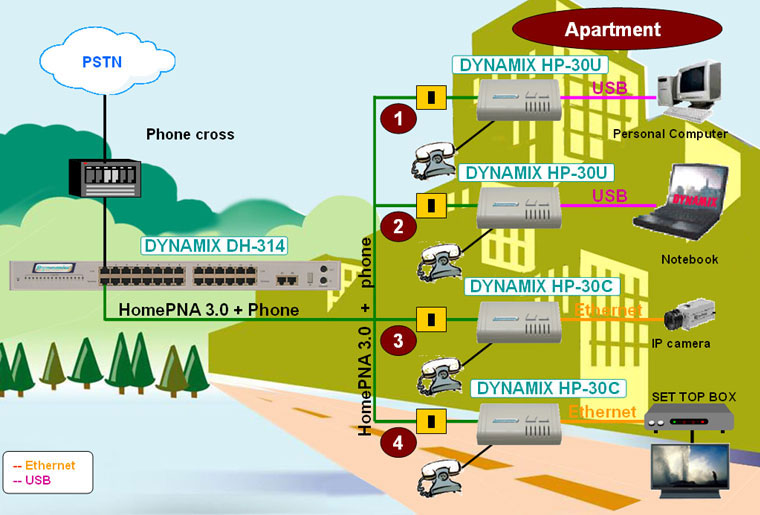
- Technology, a standard that allows a household to use a home’s existing telephone wiring for a home network. The HomePNA Alliance (formerly the Home Phoneline Networking Alliance, also known as HPNA) is an incorporated non-profit industry association of companies that develops and standardizes technology for home networking over the existing coaxial cables and telephone wiring within homes. en.wikipedia.org/wiki/HomePNA
- HOMEPLUG: USING THE HOME’S EXISTING ELECTRIC-POWER WIRING
- Technology is a standard that allows users to send data over a home’s existing electrical (AC) power lines. HomePlug is the name of the specification that defines the home networking technology that connects devices to each other through the power lines in a home (see power line networking). http://www.webopedia.com/TERM/H/HomePlug.html

- Technology is a standard that allows users to send data over a home’s existing electrical (AC) power lines. HomePlug is the name of the specification that defines the home networking technology that connects devices to each other through the power lines in a home (see power line networking). http://www.webopedia.com/TERM/H/HomePlug.html
Wireless Communications Media
The Electromagnetic Spectrum, the Radio-Frequency (RF) Spectrum, & Bandwidth
What is the electromagnetic spectrum, and how do electromagnetic waves differ?
- THE ELECTROMAGNETIC SPECTRUM
- Is the basis for all telecommunications signals, carried by both wired and wireless media. The “electromagnetic spectrum” of an object has a different meaning, and is instead the characteristic distribution of electromagnetic radiation emitted or absorbed by that particular object. http://en.wikipedia.org/wiki/Electromagnetic_spectrum

- Radio-frequency (RF) spectrum fields of electrical energy and magnetic energy that carry most communications signals. The entire spectrum of electromagnetic frequencies used for communications; includes frequencies used for radio and radar and television. http://www.thefreedictionary.com/radio-frequency+spectrum

- Is the basis for all telecommunications signals, carried by both wired and wireless media. The “electromagnetic spectrum” of an object has a different meaning, and is instead the characteristic distribution of electromagnetic radiation emitted or absorbed by that particular object. http://en.wikipedia.org/wiki/Electromagnetic_spectrum
- BANDWIDTH
- Is the range, or band, of frequencies that a transmission medium can carry in a given period of time. The amount of data that can be transmitted in a fixed amount of time. For digital devices, the bandwidth is usually expressed in bits per second(bps) or bytes per second. http://www.webopedia.com/TERM/B/bandwidth.html

“The wider a medium’s bandwidth, the more frequencies it can use to transmit data and thus the faster the transmission.”
- There are three general classes of bandwidth−narrow, and broad−which can be expressed in hertz but also in bits per second
- Narrowband
- Also known as voiceband, is used for regular telephone communications. Narrowband refers to data communication and telecommunications tools, technologies and services that utilize a narrower set or band of frequencies in the communication channel. These utilize the channel frequency that is considered flat or which will use a lesser number of frequency sets. http://www.techopedia.com/definition/8497/narrowband
- Also known as voiceband, is used for regular telephone communications. Narrowband refers to data communication and telecommunications tools, technologies and services that utilize a narrower set or band of frequencies in the communication channel. These utilize the channel frequency that is considered flat or which will use a lesser number of frequency sets. http://www.techopedia.com/definition/8497/narrowband
- Medium band
- Is used for transmitting data over long distances and for connecting mainframe and midrange computers. The medium can be coaxial cable, optical fiber, twisted pair, DSL local telephone networks or wireless broadband. http://en.wikipedia.org/wiki/Broadband

- Is used for transmitting data over long distances and for connecting mainframe and midrange computers. The medium can be coaxial cable, optical fiber, twisted pair, DSL local telephone networks or wireless broadband. http://en.wikipedia.org/wiki/Broadband
- Broadband
- Is used to transmit high-speed data and high-quality audio and video. The term broadband is used to describe a type of data transmission in which a single medium (wire) can carry several channels at once. http://www.webopedia.com/TERM/B/broadband.html

- Is used to transmit high-speed data and high-quality audio and video. The term broadband is used to describe a type of data transmission in which a single medium (wire) can carry several channels at once. http://www.webopedia.com/TERM/B/broadband.html
- Narrowband
- Is the range, or band, of frequencies that a transmission medium can carry in a given period of time. The amount of data that can be transmitted in a fixed amount of time. For digital devices, the bandwidth is usually expressed in bits per second(bps) or bytes per second. http://www.webopedia.com/TERM/B/bandwidth.html
- WAP: WIRELESS APPLICATION PROTOCOL
- WAP is designed to link nearly all mobile devices to your telecommunications carrier’s wireless network and content providers. Wireless Application Protocol (WAP) is a technical standard for accessing information over a mobile wireless network. A WAP browser is a web browser for mobile devices such as mobile phones that uses the protocol. en.wikipedia.org/wiki/Wireless_Application_Protocol

- WAP is designed to link nearly all mobile devices to your telecommunications carrier’s wireless network and content providers. Wireless Application Protocol (WAP) is a technical standard for accessing information over a mobile wireless network. A WAP browser is a web browser for mobile devices such as mobile phones that uses the protocol. en.wikipedia.org/wiki/Wireless_Application_Protocol
Four Types of Wireless Communications Media
What are the differences between the four types of wireless communications media?
- INFRARED TRANSMISSION
- Sends data signals using infrared-light waves at a frequency too low (1-4 megabits per second) for human eyes to receives and interpret. Infrared transmission refers to energy in the region of the electromagnetic radiation spectrum at wavelengths longer than those of visible light, but shorter than those of radio waves. Correspondingly,infrared frequencies are higher than those of microwaves, but lower than those of visible light. searchnetworking.techtarget.com/definition/infrared-transmission

- Sends data signals using infrared-light waves at a frequency too low (1-4 megabits per second) for human eyes to receives and interpret. Infrared transmission refers to energy in the region of the electromagnetic radiation spectrum at wavelengths longer than those of visible light, but shorter than those of radio waves. Correspondingly,infrared frequencies are higher than those of microwaves, but lower than those of visible light. searchnetworking.techtarget.com/definition/infrared-transmission
- BROADCAST RADIO
- A wireless transmission medium that sends data over long distances at up to 2 megabits per second−between regions, states, or countries. To communicate or transmit (a signal, a message, or content, such as audio or video programming) to numerous recipients simultaneously over a communication network. http://www.yourdictionary.com/broadcast

- A wireless transmission medium that sends data over long distances at up to 2 megabits per second−between regions, states, or countries. To communicate or transmit (a signal, a message, or content, such as audio or video programming) to numerous recipients simultaneously over a communication network. http://www.yourdictionary.com/broadcast
- MICROWAVE RADIO
- Transmits voice and data at 45 megabits per second through the atmosphere as superhigh-frequency radio waves called microwaves, which vibrates at 1 gigahertz (1 billion hertz) per second or higher. Relating to or being electromagnetic radiation between radio waves and infrared waves in the electromagnetic spectrum, having frequencies between 300 megahertz and 300 gigahertz and wavelengths between 1 meter and 1 millimeter. http://www.yourdictionary.com/microwave

- Transmits voice and data at 45 megabits per second through the atmosphere as superhigh-frequency radio waves called microwaves, which vibrates at 1 gigahertz (1 billion hertz) per second or higher. Relating to or being electromagnetic radiation between radio waves and infrared waves in the electromagnetic spectrum, having frequencies between 300 megahertz and 300 gigahertz and wavelengths between 1 meter and 1 millimeter. http://www.yourdictionary.com/microwave
- COMMUNICATIONS SATELLITES
- Are microwave relay stations in orbit around the earth. Often abbreviated as comsat, a communications satellite is a satellite that has been stationed in space for the purpose of providing telecommunications. Communications satellites are commonly used for mobile phone signals, weather tracking, or broadcasting television programs. Communications satellites are artificial satellites that relay receive signals from an earth stationand then retransmits the signal to other earth stations. They commonly move in a geostationary orbit. http://www.webopedia.com/TERM/C/communications_satellite.html

- Satellite system may occur one of three zones in space: GEO, MEO, and LEO
- GEO
- The highest level known as geostationary earth orbit (GEO). An orbit whose position in the sky remains the same for a stationary observer on earth. This effect is achieved with a circular orbit 35,786 kilometers (22,236 mi) above the Earth’s equator and following the direction of the Earth’s rotation. An object in such an orbit has an orbital period equal to the Earth’s rotational period (one sidereal day), and thus appears motionless at a fixed position in the sky to ground observers. Communications satellites and weather satellites are often placed in geostationary orbits, so that the satellite antennas which communicate with them do not have to rotate to track them, but can be pointed permanently at the position in the sky where they stay. Using this characteristic, ocean color satellites with visible sensors (e.g. the Geostationary Ocean Color Imager (GOCI)) can also be operated in geostationary orbit in order to monitor sensitive changes of ocean environments. http://en.wikipedia.org/wiki/Geostationary_orbit
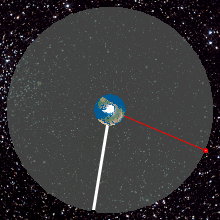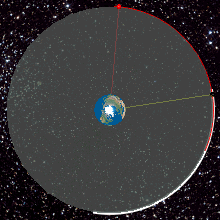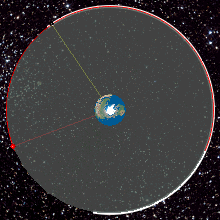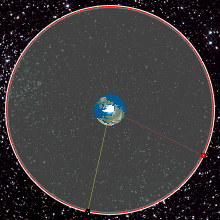

- The highest level known as geostationary earth orbit (GEO). An orbit whose position in the sky remains the same for a stationary observer on earth. This effect is achieved with a circular orbit 35,786 kilometers (22,236 mi) above the Earth’s equator and following the direction of the Earth’s rotation. An object in such an orbit has an orbital period equal to the Earth’s rotational period (one sidereal day), and thus appears motionless at a fixed position in the sky to ground observers. Communications satellites and weather satellites are often placed in geostationary orbits, so that the satellite antennas which communicate with them do not have to rotate to track them, but can be pointed permanently at the position in the sky where they stay. Using this characteristic, ocean color satellites with visible sensors (e.g. the Geostationary Ocean Color Imager (GOCI)) can also be operated in geostationary orbit in order to monitor sensitive changes of ocean environments. http://en.wikipedia.org/wiki/Geostationary_orbit
- MEO
- The medium-earth orbit (MEO) is 5,000-10,000 miles. Medium Earth orbit (MEO), sometimes called intermediate circular orbit (ICO), is the region of space around the Earth above low Earth orbit (altitude of 2,000 kilometres (1,243 mi)) and below geostationary orbit (altitude of 35,786 kilometres (22,236 mi)). http://en.wikipedia.org/wiki/Medium_Earth_orbit

- The medium-earth orbit (MEO) is 5,000-10,000 miles. Medium Earth orbit (MEO), sometimes called intermediate circular orbit (ICO), is the region of space around the Earth above low Earth orbit (altitude of 2,000 kilometres (1,243 mi)) and below geostationary orbit (altitude of 35,786 kilometres (22,236 mi)). http://en.wikipedia.org/wiki/Medium_Earth_orbit
- LEO
- The low-earth orbit (LEO) is 200-1,000 miles. A low Earth orbit (LEO) is an orbit around Earth with an altitude between 160 kilometers (99 mi), (orbital period of about 88 minutes), and 2,000 kilometers (1,200 mi) (about 127 minutes). Objects below approximately 160 kilometers (99 mi) will experience very rapid orbitaldecay and altitude loss. en.wikipedia.org/wiki/Low_Earth_orbit

- The low-earth orbit (LEO) is 200-1,000 miles. A low Earth orbit (LEO) is an orbit around Earth with an altitude between 160 kilometers (99 mi), (orbital period of about 88 minutes), and 2,000 kilometers (1,200 mi) (about 127 minutes). Objects below approximately 160 kilometers (99 mi) will experience very rapid orbitaldecay and altitude loss. en.wikipedia.org/wiki/Low_Earth_orbit
- GEO
- Are microwave relay stations in orbit around the earth. Often abbreviated as comsat, a communications satellite is a satellite that has been stationed in space for the purpose of providing telecommunications. Communications satellites are commonly used for mobile phone signals, weather tracking, or broadcasting television programs. Communications satellites are artificial satellites that relay receive signals from an earth stationand then retransmits the signal to other earth stations. They commonly move in a geostationary orbit. http://www.webopedia.com/TERM/C/communications_satellite.html
Long-Distance Wireless: One-Way Communication
How do the Global Positioning System and one-way pager systems work?
- THE GLOBAL POSITIONING SYSTEM
- Consists of 24 earth-orbiting satellites continuously transmitting timed radio signals that can be used to identify earth locations. The Global Positioning System (GPS) is a space-based satellite navigation system that provides location and time information in all weather conditions, anywhere on or near the Earth where there is an unobstructed line of sight to four or more GPS satellites. en.wikipedia.org/wiki/Global_Positioning_System

- How GPS works
- The uses of GPS
- The limitations of GPS
- Consists of 24 earth-orbiting satellites continuously transmitting timed radio signals that can be used to identify earth locations. The Global Positioning System (GPS) is a space-based satellite navigation system that provides location and time information in all weather conditions, anywhere on or near the Earth where there is an unobstructed line of sight to four or more GPS satellites. en.wikipedia.org/wiki/Global_Positioning_System
- ONE-WAY PAGERS
- Pagers are simple radio receivers that receives data sent from a special radio transmitter. A wireless telecommunications device that receives and displays numeric or text messages, or receives and announces voice messages. One-way pagers can only receive messages, while response pagers and two-way pagers can also acknowledge, reply to, and originate messages using an internal transmitter.[1] Pagers operate as part of a paging system which includes one or more fixed transmitters (or in the case of response pagers and two-way pagers, one or more base stations), as well as a number of pagers carried by mobile users. These systems can range from a restaurant system with a single low-power transmitter, to a nationwide system with thousands of high-power base stations. http://en.wikipedia.org/wiki/Pager
- How a pager works
- The uses of pagers
- Pagers are simple radio receivers that receives data sent from a special radio transmitter. A wireless telecommunications device that receives and displays numeric or text messages, or receives and announces voice messages. One-way pagers can only receive messages, while response pagers and two-way pagers can also acknowledge, reply to, and originate messages using an internal transmitter.[1] Pagers operate as part of a paging system which includes one or more fixed transmitters (or in the case of response pagers and two-way pagers, one or more base stations), as well as a number of pagers carried by mobile users. These systems can range from a restaurant system with a single low-power transmitter, to a nationwide system with thousands of high-power base stations. http://en.wikipedia.org/wiki/Pager
Long-Distance Wireless: Two-Way Communication
How do I distinguish among five types of long-distance wireless technologies?
- TWO-WAY PAGERS & WIRELESS EMAIL DEVICES: BLACKBERRY
- IG (FIRST-GENERATION) CELLULAR SERVICE: ANALOG CELLPHONES
- Analog cellphones are designed primarily for communicating by voice through a system of ground-area cells. Each cells is hexagonal in shape, usually 8 miles or less in diameter, and is served by a transmitter-receiving tower

- Analog cellphones are designed primarily for communicating by voice through a system of ground-area cells. Each cells is hexagonal in shape, usually 8 miles or less in diameter, and is served by a transmitter-receiving tower
- 2G (SECOND-GENERATION) WIRELESS SERVICES: DIGITAL CELLPHONES & PDAS
- Digital wireless services − which support digital cellphones and personal digital assistants−use a network of cell towers to send voice communications and data over the airwaves in digital form

- CDMA: Code Division Multiple Access. Code division multiple access (CDMA) is a channel access method used by various radio communication technologies. CDMA is an example of multiple access, which is where several transmitters can send information simultaneously over a single communication channel. en.wikipedia.org/wiki/Code_division_multiple_access

- GSM: Global System for Mobile Communications. GSM (Global System for Mobile Communications, originally Groupe Spécial Mobile), is a standard developed by the European Telecommunications Standards Institute (ETSI) to describe protocols for second generation (2G) digital cellular networks used by mobile phones. en.wikipedia.org/wiki/GSM

- Digital wireless services − which support digital cellphones and personal digital assistants−use a network of cell towers to send voice communications and data over the airwaves in digital form
- 2.5G WIRELESS DIGITAL SERVICES
- 3G (THIRD-GENERATION) WIRELESS DIGITAL SERVICES

- EV-DO: Evolution Data Only has average speeds of 400-700 kilobits per second, with peaks of 2 megabits. Evolution Data Only (EVDO) is now called Evolution-DataOptimized (EV-DO). Evolution–Data Optimized (EV-DO) is a fast wireless broadband access (3G), where you are the hotspot (meaning you don’t need a Wi-Fi hotspot to have the Internet access). Your PC or laptop requires a EVDO PC card for connection. EV-DO supports an “always-on” connection, similar to DSL. http://www.webopedia.com/TERM/E/Evolution_Data_Optimized.html

- UMTS: Universal Mobile Telecommunications Systems has average speeds of 22-=320 kilobits per second. A third generation mobile cellular system for networks based on the GSM standard. Developed and maintained by the 3GPP (3rd Generation Partnership Project), UMTS is a component of the International Telecommunications Union IMT-2000 standard set and compares with the CDMA2000 standard set for networks based on the competing cdmaOne technology. UMTS uses wideband code division multiple access (W-CDMA) radio access technology to offer greater spectral efficiency and bandwidth to mobile network operators. http://en.wikipedia.org/wiki/Universal_Mobile_Telecommunications_System

- EV-DO: Evolution Data Only has average speeds of 400-700 kilobits per second, with peaks of 2 megabits. Evolution Data Only (EVDO) is now called Evolution-DataOptimized (EV-DO). Evolution–Data Optimized (EV-DO) is a fast wireless broadband access (3G), where you are the hotspot (meaning you don’t need a Wi-Fi hotspot to have the Internet access). Your PC or laptop requires a EVDO PC card for connection. EV-DO supports an “always-on” connection, similar to DSL. http://www.webopedia.com/TERM/E/Evolution_Data_Optimized.html
- WIMAX: PROMISING NEW LONG-DISTANCE WIRELESS STANDARD
Short-Range Wireless: Two-Way Communication
How do I distinguish among the three types of short-range wireless technologies?
-
- Local area networks−range 50-150 feet: These include the popular Wi-Fi standard. A computer network that interconnects computers within a limited area such as a home, school, computer laboratory, or office building, using network media.[1] The defining characteristics of LANs, in contrast to wide area networks (WANs), include their smaller geographic area, and non-inclusion of leased telecommunication lines. http://en.wikipedia.org/wiki/Local_area_network

- Personal area networks−range 30-32 feet: These use Bluetooth, ultra wideband, and wireless USB. A personal area network (PAN) is a computer network used for data transmission among devices such as computers, telephones and personal digital assistants. en.wikipedia.org/wiki/Personal_area_network

- Home automation networks−range 100-250 feet: These use the Insteon, ZigBee, and Z-Wave standards. Home automation may include centralized control of lighting, HVAC (heating, ventilation and air conditioning), appliances, security locks of gates and doors and other systems, to provide improved convenience, comfort, energy efficiency and security. http://en.wikipedia.org/wiki/Home_automation

- Local area networks−range 50-150 feet: These include the popular Wi-Fi standard. A computer network that interconnects computers within a limited area such as a home, school, computer laboratory, or office building, using network media.[1] The defining characteristics of LANs, in contrast to wide area networks (WANs), include their smaller geographic area, and non-inclusion of leased telecommunication lines. http://en.wikipedia.org/wiki/Local_area_network
- SHORT-RANGE WIRELESS FOR LOCAL AREA NETWORKS: WI-FI B, A, G, & N
- Wi-Fi b, a, and g
- Wi-Fi n with MIMO: MIMO (“my-moh” and for short for “multiple input multiple output“). In radio, multiple–input and multiple–output, or MIMO (pronounced as “my-moh” or “me-moh”), is the use of multiple antennas at both the transmitter and receiver to improve communication performance. en.wikipedia.org/wiki/MIMO

- SHORT-RANGE WIRELESS FOR PERSONAL AREA NETWORKS: BLUETOOTH, ULTRA WIDEBAND, & WIRELESS USB
- Bluetooth: is a short-range wireless digital standard aimed at linking cellphones, PDAs, computers, and peripherals up to distances of 30 feet. A wireless technology standard for exchanging data over short distances (using short-wavelength UHF radio waves in the ISM band from 2.4 to 2.485 GHz) from fixed and mobile devices, and building personal area networks (PANs). http://en.wikipedia.org/wiki/Bluetooth

- Ultra wideband (UWB) is a promising technology operating in the range of 480 megabits per second up to 30 feet that uses a low power source to send out millions of bursts of radio energy every second over many different frequencies, which are then reassembled by a UWB receiver. A communications technology that employs a wide bandwidth (typically defined as greater than 20% of the center frequency or 500MHz). UWB is usually used in short-range wireless applications but can be sent over wires. http://www.maximintegrated.com/en/glossary/definitions.mvp/term/Ultra-Wideband/gpk/987

- Wireless USB: would have a typical range of 32 feet and a maximum data rate of 480 megabits per second. A form of Universal Serial Bus ( USB ) technology that uses radio-frequency ( RF ) links rather than cables to provide the interfaces between a computer and peripherals, such as monitors, printers, external drives, head sets, MP3 players and digital cameras. whatis.techtarget.com/definition/wireless–USB-WUSB

- Bluetooth: is a short-range wireless digital standard aimed at linking cellphones, PDAs, computers, and peripherals up to distances of 30 feet. A wireless technology standard for exchanging data over short distances (using short-wavelength UHF radio waves in the ISM band from 2.4 to 2.485 GHz) from fixed and mobile devices, and building personal area networks (PANs). http://en.wikipedia.org/wiki/Bluetooth
- SHORT-RANGE WIRELESS FOR HOME AUTOMATION NETWORKS: INSERTION, ZIGBEE, & Z-WAVE
- Insteon – Insteon is a home area networking technology developed primarily for connecting light switches and loads. Insteon devices send messages either via the power line, or by means of radio frequency (RF) waves, or both (dual-band).
https://github.com/openhab/openhab/wiki/Insteon-PLM-Binding
- Zigbee – ZigBee is a specification for a suite of high-level communication protocols used to create personal area networks built from small, low-power digital radios. ZigBee is based on an IEEE 802.15 standard. en.wikipedia.org/wiki/ZigBee

- Z-wave – Z–Wave is a wireless communications protocol designed for home automation, specifically for remote control applications in residential and light commercial environments. en.wikipedia.org/wiki/Z–Wave

- Insteon – Insteon is a home area networking technology developed primarily for connecting light switches and loads. Insteon devices send messages either via the power line, or by means of radio frequency (RF) waves, or both (dual-band).
Cyberthreats, Hackers, & Safeguards
What are areas I should be concerned about for keeping my computer system secure?
- Cyber threats: denial-of-service attacks, worms, viruses, and Trojan horses. Cyber threats to a control system refer to persons who attempt unauthorized access to a control system device and/or network using a data communications pathway. This access can be directed from within an organization by trusted users or from remote locations by unknown persons using the Internet. https://ics-cert.us-cert.gov/content/cyber-threat-source-descriptions

- Perpetrators of cyber mischief: hackers and crackers

- Computer safety: antivirus software, firewalls, passwords, biometric authentication, and encryption

Cyber Threats: Denial-of-Service Attacks, Worms, Viruses, & Trojan Horses
What are denial-of-service attacks, worms, viruses, & Trojan horses?
- DENIAL-OF-SERVICE ATTACKS
- DoS attack consists of making repeated requests of a computer system or network, thereby over-loading it and denying legitimate users access to it. In computing, a denial-of-service (DoS) or distributed denial-of-service (DDoS) attack is an attempt to make a machine or network resource unavailable to its intended users. en.wikipedia.org/wiki/Denial-of-service_attack


- DoS attack consists of making repeated requests of a computer system or network, thereby over-loading it and denying legitimate users access to it. In computing, a denial-of-service (DoS) or distributed denial-of-service (DDoS) attack is an attempt to make a machine or network resource unavailable to its intended users. en.wikipedia.org/wiki/Denial-of-service_attack
- WORMS
- Is a program that copies itself repeatedly into a computer’s memory or into a disk drive. A program or algorithm that replicates itself over a computer network and usually performs malicious actions, such as using up the computer’s resources and possibly shutting the system down. http://www.webopedia.com/TERM/W/worm.html
- VIRUSES
- Is a “deviant” program, stored on a computer floppy disk, hard drive, or CD, that can cause unexpected and often undesirable effects,such as destroying or corrupting data. A computer virus is a program or piece of code that is loaded onto your computer without your knowledge and runs against your wishes. Viruses can also replicate themselves. All computer viruses are man-made. A simple virus that can make a copy of itself over and over again is relatively easy to produce. Even such a simple virus is dangerous because it will quickly use all available memory and bring the system to a halt. An even more dangerous type of virus is one capable of transmitting itself across networks and bypassing security systems. http://www.webopedia.com/TERM/V/virus.html
- TROJAN HORSES
- Is a program that pretends to be useful program, usually free, such as a game or sccreen saver, but carries viruses, or destructive instructions, that perpetuate mischief without your knowledge. A destructive program that masquerades as a benign application. Unlike viruses, Trojan horses do not replicate themselves but they can be just as destructive. One of the most insidious types of Trojan horse is a program that claims to rid your computer of viruses but instead introduces viruses onto your computer. http://www.webopedia.com/TERM/T/Trojan_horse.html
- HOW MALWARE IS SPREAD
- By infected floppies or CDs
- By opening unknown email attachments
- By clicking on infiltrated websites
- Through infiltrated WI-Fi hot spots
Some Cyber Villains: Hackers & Crackers
What are the various kinds of hackers and crackers?
- HACKERS
- Are defined (1) as computer enthusiasts, people who enjoy learning programming languages and computer systems, but also (2) as people who gain unauthorized access to computers or networks, often just for the challenge of it. A slang term for a computer enthusiast, i.e., a person who enjoys learning programming languages and computer systems and can often be considered an expert on the subject(s). Among professional programmers, depending on how it used, the term can be either complimentary or derogatory, although it is developing an increasingly derogatory connotation. http://www.webopedia.com/TERM/H/hacker.html
- Thrill-seekers hackers
- White-hat seekers


- Are defined (1) as computer enthusiasts, people who enjoy learning programming languages and computer systems, but also (2) as people who gain unauthorized access to computers or networks, often just for the challenge of it. A slang term for a computer enthusiast, i.e., a person who enjoys learning programming languages and computer systems and can often be considered an expert on the subject(s). Among professional programmers, depending on how it used, the term can be either complimentary or derogatory, although it is developing an increasingly derogatory connotation. http://www.webopedia.com/TERM/H/hacker.html
- CRACKERS
- Are malicious hackers, people who break into computers for malicious purposes. To break into a computer system. The term was coined in the mid-80s by hackers who wanted to differentiate themselves from individuals whose sole purpose is to sneak through security systems. Whereas crackers sole aim is to break into secure systems, hackers are more interested in gaining knowledge about computer systems and possibly using this knowledge for playful pranks. Although hackers still argue that there’s a big difference between what they do and what crackers do, the mass media has failed to understand the distinction, so the two terms — hack and crack — are often used interchangeably. http://www.webopedia.com/TERM/C/crack.html
- Scripts kiddies
- Hacktivists
- Black-hat hackers
- Cyberterrorists

- Are malicious hackers, people who break into computers for malicious purposes. To break into a computer system. The term was coined in the mid-80s by hackers who wanted to differentiate themselves from individuals whose sole purpose is to sneak through security systems. Whereas crackers sole aim is to break into secure systems, hackers are more interested in gaining knowledge about computer systems and possibly using this knowledge for playful pranks. Although hackers still argue that there’s a big difference between what they do and what crackers do, the mass media has failed to understand the distinction, so the two terms — hack and crack — are often used interchangeably. http://www.webopedia.com/TERM/C/crack.html
Online Safety: Antivirus Software, Firewalls, Passwords, Biometric Authentication, & Encryption
What should I be doing to keep my computer safe against cyber threats?
- ANTIVIRUS SOFTWARE
- Scans a computer’s hard disk, floppy disks and CDs, and main memory to detect viruses and, sometimes, to destroy them. Antivirus or anti-virus software (often abbreviated as AV), sometimes known as anti-malware software, is computer software used to prevent, detect and remove malicious software. Antivirus software was originally developed to detect and remove computer viruses, hence the name. en.wikipedia.org/wiki/Antivirus_software


- Scans a computer’s hard disk, floppy disks and CDs, and main memory to detect viruses and, sometimes, to destroy them. Antivirus or anti-virus software (often abbreviated as AV), sometimes known as anti-malware software, is computer software used to prevent, detect and remove malicious software. Antivirus software was originally developed to detect and remove computer viruses, hence the name. en.wikipedia.org/wiki/Antivirus_software
- FIREWALLS
- Is a system of hardware and/or software that protects a computer or a network from intruders. A firewall is a system designed to prevent unauthorized access to or from a private network. Firewalls can be implemented in both hardware and software, or a combination of both. Firewalls are frequently used to prevent unauthorized Internet users from accessing private networks connected to the Internet, especially intranets. All messages entering or leaving the intranet pass through the firewall, which examines each message and blocks those that do not meet the specified security criteria. http://www.webopedia.com/TERM/F/firewall.html

- If you have one computer−software firewall
- If you have more than one computer−hardware firewall
- Is a system of hardware and/or software that protects a computer or a network from intruders. A firewall is a system designed to prevent unauthorized access to or from a private network. Firewalls can be implemented in both hardware and software, or a combination of both. Firewalls are frequently used to prevent unauthorized Internet users from accessing private networks connected to the Internet, especially intranets. All messages entering or leaving the intranet pass through the firewall, which examines each message and blocks those that do not meet the specified security criteria. http://www.webopedia.com/TERM/F/firewall.html
- PASSWORDS
- BIOMETRIC AUTHENTICATION
- Biometrics the science of measuring individual body characteristics. Biometrics is the science and technology of measuring and analyzing biological data. In information technology, biometrics refers to technologies that measure and analyze human body characteristics, such as DNA, fingerprints, eye retinas and irises, voice patterns, facial patterns and hand measurements, for authentication purposes. http://searchsecurity.techtarget.com/definition/biometrics
- Hand-geometry systems
- Fingerprint scanners
- Iris-recognition systems
- Face-recognition systems
- Voice-recognition systems

- Biometrics the science of measuring individual body characteristics. Biometrics is the science and technology of measuring and analyzing biological data. In information technology, biometrics refers to technologies that measure and analyze human body characteristics, such as DNA, fingerprints, eye retinas and irises, voice patterns, facial patterns and hand measurements, for authentication purposes. http://searchsecurity.techtarget.com/definition/biometrics
- ENCRYPTION
- Is the process of altering readable data into unreadable form to prevent unauthorized access. Encryption is the most effective way to achieve data security. To read an encrypted file, you must have access to a secret key or password that enables you to decrypt it. Unencrypted data is called plain text ; encrypted data is referred to as cipher text. http://www.webopedia.com/TERM/E/encryption.html

- Private key – A private key is a tiny bit of code that is paired with a public key to set off algorithms for text encryption and decryption. It is created as part of public key cryptography during asymmetric-key encryption and used to decrypt and transform a message to a readable format. Public and private keys are paired for secure communication, such as email. A private key is also known as a secret key. http://www.techopedia.com/definition/16135/private-key
- Public key – A public key is created in public key encryption cryptography that uses asymmetric-key encryption algorithms. Public keys are used to convert a message into an unreadable format. Decryption is carried out using a different, but matching, private key. Public and private keys are paired to enable secure communication. http://www.techopedia.com/definition/16139/public-key
- Is the process of altering readable data into unreadable form to prevent unauthorized access. Encryption is the most effective way to achieve data security. To read an encrypted file, you must have access to a secret key or password that enables you to decrypt it. Unencrypted data is called plain text ; encrypted data is referred to as cipher text. http://www.webopedia.com/TERM/E/encryption.html

